New Updated N10-007 Exam Questions from PassLeader N10-007 PDF dumps! Welcome to download the newest PassLeader N10-007 VCE dumps: https://www.passleader.com/n10-007.html (712 Q&As)
Keywords: N10-007 exam dumps, N10-007 exam questions, N10-007 VCE dumps, N10-007 PDF dumps, N10-007 practice tests, N10-007 study guide, N10-007 braindumps, CompTIA Network+ Certification Exam
P.S. Free N10-007 dumps download from Google Drive: https://drive.google.com/open?id=18G7nZoCo1Rl5qL3FXrR-6O-5qSmfy7ty
NEW QUESTION 678
A network administrator is installing a campus network of two routers, 24 switches, 76 APs, and 492 VoIP phone sets. Which of the following additional devices should the administrator install to help manage this network?
A. VoIP PBX
B. Content filter
C. RADIUS server
D. Wireless controller
Answer: D
NEW QUESTION 679
A technician arrives at a new building to find cabling has been run and terminated, but only the wall ports have been labeled. Which of the following tools should be utilized to BEST facilitate labeling the patch panel?
A. Tone generator
B. Cable tester
C. Multimeter
D. Loopback adapter
Answer: B
NEW QUESTION 680
Which of the following policies prohibits a network administrator from using spare servers in the datacenter to mine bitcoins?
A. NDA
B. BYOD
C. AUP
D. MOU
Answer: C
NEW QUESTION 681
Which of the following technologies is used when multiple Ethernet adapters work to increase speed and fault tolerance?
A. Clustering
B. Load balancing
C. Redundant circuits
D. NIC teaming
Answer: D
NEW QUESTION 682
A network technician has finished configuring a new DHCP for a network. To ensure proper functionality, which of the following ports should be allowed on the server’s local firewall? (Choose two.)
A. 20
B. 21
C. 53
D. 67
E. 68
F. 389
Answer: DE
NEW QUESTION 683
A new technician is connecting an access switch to a distribution switch uplink in a datacenter using fiber cables. Which of the following are transceivers the technician should use to perform this job? (Choose two.)
A. RJ45
B. DB-9
C. LC
D. SFTP
E. GBIC
F. SC
Answer: CF
NEW QUESTION 684
Which of the following physical security devices is used to prevent unauthorized access into a datacenter?
A. Motion detector
B. Video camera
C. Asset tracking
D. Smart card reader
Answer: D
NEW QUESTION 685
A technician is installing two new servers that collect logs. After installing the servers, the technician reviews the logical output from various commands. Which of the following should be included in a logical network diagram?
A. Rack location
B. Room number
C. Media type
D. Hostname
Answer: D
NEW QUESTION 686
A few weeks after starting a new position, Joe, a junior network administrator, receives a call from an internal number asking for his username and password to update some records. Joe realizes this may be a type of attack on the network, since he has full access to network resources. Which of the following attacks is described?
A. Logic bomb
B. Social engineering
C. Trojan horse
D. Insider threat
Answer: B
NEW QUESTION 687
A technician is sent to troubleshoot a faulty network connection. The technician tests the cable, and data passes through successfully. No changes were made in the environment, however, when a network device is connected to the switch using the cable, the switchport will not light up. Which of the following should the technician attempt NEXT?
A. Modify the speed and duplex
B. Plug in to another port
C. Replace the NIC
D. Change the switch
Answer: B
NEW QUESTION 688
A technician has been assigned to capture packets on a specific switchport. Which of the following switch feature MUST be used to accomplish this?
A. Spanning tree
B. Trunking
C. Port aggregation
D. Port mirroring
Answer: D
NEW QUESTION 689
Which of the following operate only within the UDP protocol?
A. Frames
B. Datagrams
C. Segments
D. Packets
Answer: B
NEW QUESTION 690
An employee reports an error when visiting a website using SSL, and a message is displayed warning of an invalid certificate. Which of the following could be occurring?
A. Phishing
B. DDoS
C. Evil twin
D. MITM
E. OCSP stapling
Answer: C
NEW QUESTION 691
A network technician is troubleshooting a connectivity issue and determines the cause is related to the VLAN assignment on one of the access switches in the network. After resolving the issue, the network technician decides to update the documentation to refer to the correct VLAN. Which of the following should the technician update?
A. Physical diagram
B. Logical diagram
C. IDF documentation
D. Change management documentation
E. Incident response plan
Answer: B
NEW QUESTION 692
A university has a lecture hall containing 100 students. Currently, the lecture hall has two 802.11ac wireless access points, which can accommodate up to 50 devices each. Several students report they are unable to connect devices to the wireless network. Which of the following is MOST likely the issue?
A. One of the wireless access points is on the wrong frequency.
B. The students are attempting to connect 802.11g devices.
C. The students are using more than one wireless device port seat.
D. Distance limitations are preventing the students from connecting.
Answer: D
NEW QUESTION 693
A WAP has been dropping off the network sporadically and reconnecting shortly thereafter. The Cat5 wire connecting the access point is a long run of 265ft (81m) and goes through the business area and the mechanical room. Which of the following should the technician do to fix the AP connectivity issue?
A. Install a repeater to boost the signal to its destination.
B. Replace the UTP cable with plenum cable.
C. Upgrade the cable from Cat 5 to Cat 5e.
D. Set the AP to half duplex to compensate for signal loss.
Answer: C
NEW QUESTION 694
A technician wants to configure a SOHO network to use a specific public DNS server. Which of the following network components should the technician configure to point all clients on a network to a new DNS server?
A. Router
B. Switch
C. Load balancer
D. Proxy server
Answer: A
NEW QUESTION 695
A company wishes to allow employees with company-owned mobile devices to connect automatically to the corporate wireless network upon entering the facility. Which of the following would BEST accomplish this objective?
A. Open wireless
B. Geofencing
C. Pre-shared key
D. MAC filtering
Answer: C
NEW QUESTION 696
A network engineer for a manufacturing company is implementing a wireless network that provides reliable coverage throughout the facility. There are several large, electric, motorized machines installed on the shop floor for automating the manufacturing process. These machines are known to be significant sources of RF interference. Which of the following frequencies should the wireless network use to MINIMIZE this interference?
A. 2.4 GHz
B. 56 MHz
C. 5 GHz
D. 900 MHz
Answer: C
NEW QUESTION 697
A company has procured a new office building and started the process of assigning employees to work at that location. The company has also purchased equipment for the new location. There are 5,033 laptops, 6,000 monitors, and 857 printers. Which of the following steps is the technician most likely to complete FIRST?
A. Create a rack diagram.
B. Create a network baseline.
C. Create an inventory database.
D. Create a port location diagram.
Answer: C
NEW QUESTION 698
Which of the following is created on a 48-port switch with five active VLANs?
A. 48 networks, 5 segments.
B. 48 collision domains, 5 broadcast domains.
C. 240 private networks.
D. 240 usable IP addresses.
Answer: B
NEW QUESTION 699
A corporate manager says wireless phones do not work properly inside the main building. After a troubleshooting process, the network administrator detects that the voice packets are arriving on the wireless phones with different delay times. Which of the following performance issues is the company facing?
A. Jitter
B. Latency
C. Attenuation
D. Frequency mismatch
Answer: A
NEW QUESTION 700
Which of the following technologies is used to attach multiple guest operating systems to a single physical network port?
A. Virtual switch
B. FCoE
C. VPC
D. vSAN
E. Fibre Channel
Answer: A
NEW QUESTION 701
When speaking with a client, an employee realizes a proposed solution may contain a specific cryptographic technology that is prohibited for non-domestic use. Which of the following documents or regulations should be consulted for confirmation?
A. Incident response policy
B. International export controls
C. Data loss prevention
D. Remote access policies
E. Licensing restrictions
Answer: B
NEW QUESTION 702
A network technician is installing a new network switch in the MDF. The technician is using fiber to connect the switch back to the core. Which of the following transceiver types should the technician use?
A. MT-RJ
B. BNC
C. GBIC
D. F-type
Answer: C
NEW QUESTION 703
A network technician notices a router that repeatedly reboots. When contacting technical support, the technician discovers this is a known problem in which an attacker can craft packets and send them to the router through an obsolete protocol port, causing the router to reboot. Which of the following did the network technician fail to do? (Choose two.)
A. Generate new crypto keys.
B. Keep patches updated.
C. Disable unnecessary services.
D. Shut down unused interfaces.
E. Avoid using common passwords.
F. Implement file hashing.
Answer: BC
NEW QUESTION 704
A technician has replaced a customer’s desktop with a known-good model from storage. However, the replacement desktop will not connect to network resources. The technician suspects the desktop has not been kept up to date with security patches. Which of the following is MOST likely in place?
A. ACL
B. NAC
C. Traffic shaping
D. SDN
E. NTP
Answer: B
NEW QUESTION 705
A network technician wants to gain a better understanding of network trends to determine if they are over capacity. Which of the following processes should the technician use?
A. Log review
B. Port scanning
C. Vulnerability scanning
D. Traffic analysis
Answer: D
NEW QUESTION 706
A network technician is configuring network addresses and port numbers for a router ACL to block a peer- to-peer application. Which of the following is the HIGHEST layer of the OSI model at which this router ACL operates?
A. Transport
B. Network
C. Session
D. Application
Answer: A
NEW QUESTION 707
An attacker has flooded the hardware tables of a switch to forward traffic to the attacker’s IP address rather than the default router. The traffic received is copied in real time, and then forwarded to the default router transparently from the end-user perspective. Which of the following attacks are occurring in this scenario? (Choose two.)
A. DNS poisoning
B. ARP poisoning
C. Man-in-the-middle
D. Ransomware
E. Evil twin
F. Reflective
Answer: BC
NEW QUESTION 708
Drag and Drop
You are tasked with creating a network that will accomplish the following requirements:
– The remote Sales Team must be able to connect to the corporate network.
– Each department must have ONLY two PCs and a server.
– Eqach department must be segmented from each other.
– The following VLANs have been designed:
* VLAN 2 – Finance
* VLAN 12 – Sales
* VLAN 22 – Human Resources (HR)
– Routing for VLAN 12 is implemented on the router.
– Routing for VLAN 2 and VLAN 22 is on the switch.
(Complete the network by dragging the required objects onto the diagram. Objects can be used multiple times and not all placeholders need to be filled. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.)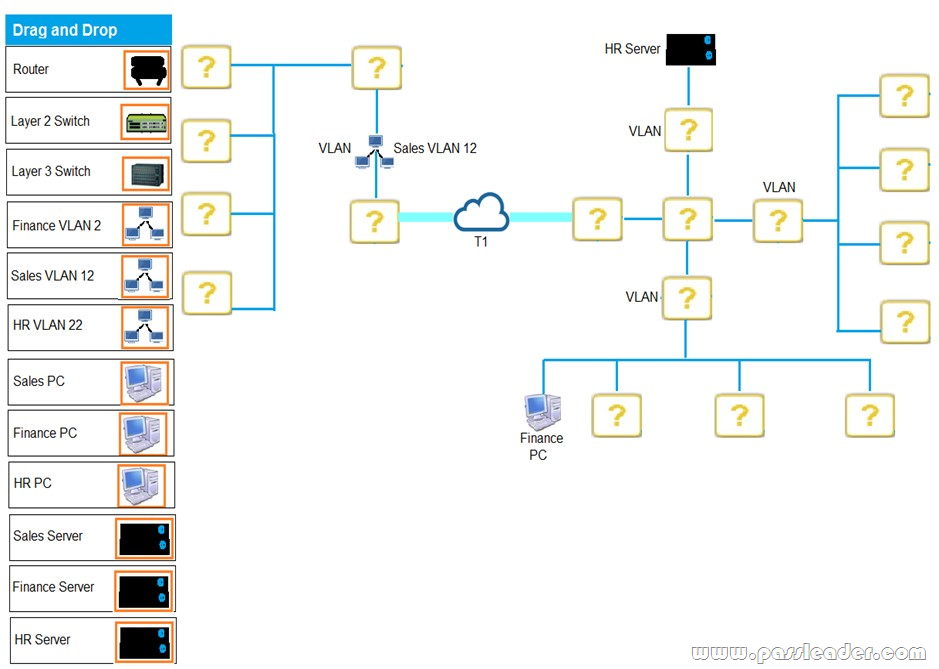
Answer: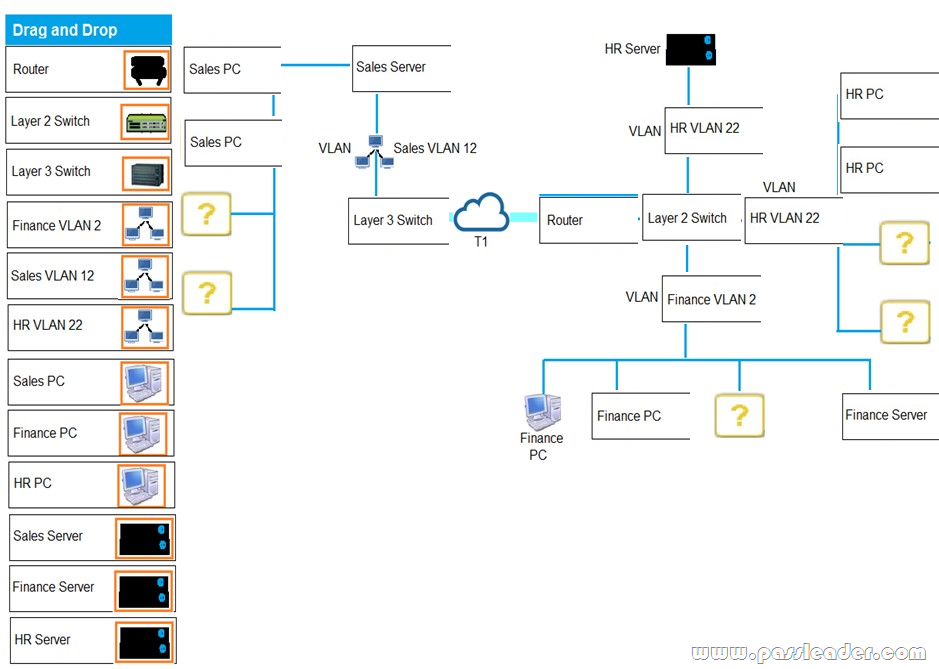
NEW QUESTION 709
A remote user is required to upload weekly reports to a server at the main office. Both the remote user and the server are using a Windows-based OS. Which of the following represents the BEST method for the remote user to connect to the server?
A. RDP
B. Telnet
C. SSH
D. VNC
Answer: A
NEW QUESTION 710
At which of the following layers of the OSI model would TCP/UDP operate?
A. Layer 3
B. Layer 4
C. Layer 5
D. Layer 6
Answer: B
NEW QUESTION 711
……
Download the newest PassLeader N10-007 dumps from passleader.com now! 100% Pass Guarantee!
N10-007 PDF dumps & N10-007 VCE dumps: https://www.passleader.com/n10-007.html (712 Q&As) (New Questions Are 100% Available and Wrong Answers Have Been Corrected! Free VCE simulator!)
P.S. Free N10-007 Exam Dumps Collection On Google Drive: https://drive.google.com/open?id=18G7nZoCo1Rl5qL3FXrR-6O-5qSmfy7ty





